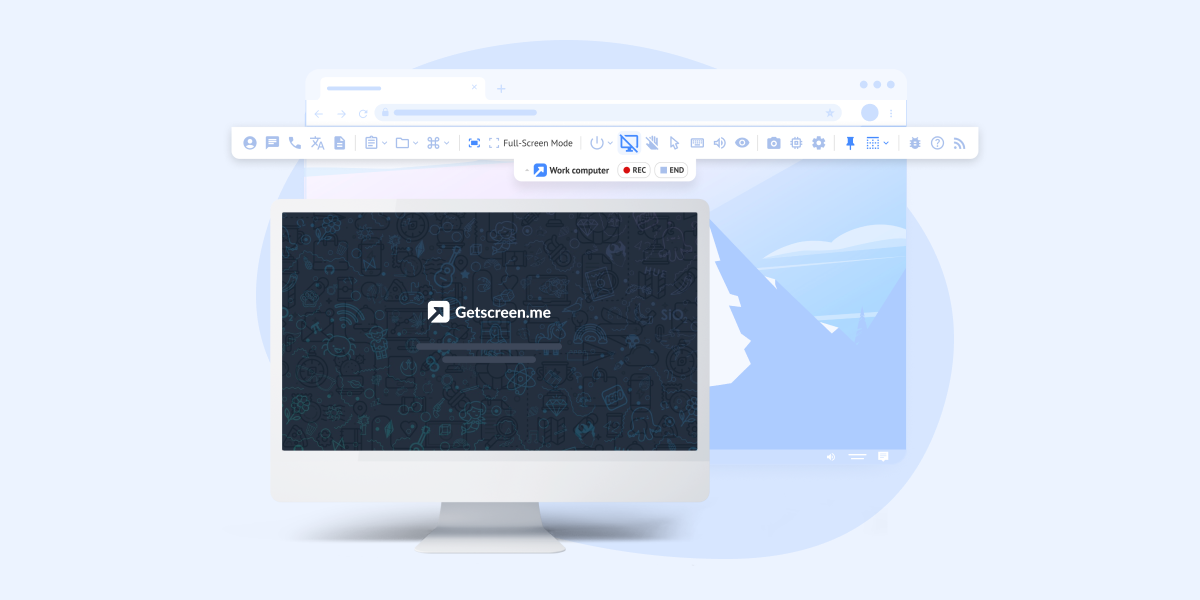
Two-Step Verification
Two-step verification adds an extra one-time code from email, Telegram, or an authenticator app, significantly increasing your account’s security. This article explains how to enable the feature and set up your preferred verification method.